Debian - nala
Nala is a modern and user-friendly front-end for the APT package manager, designed to enhance the package management experience on Debian systems
Installation
apt install nala
Check Version
nala --version
root@debianxx ~# nala --version
nala 0.15.4
Install Package
nala install btop
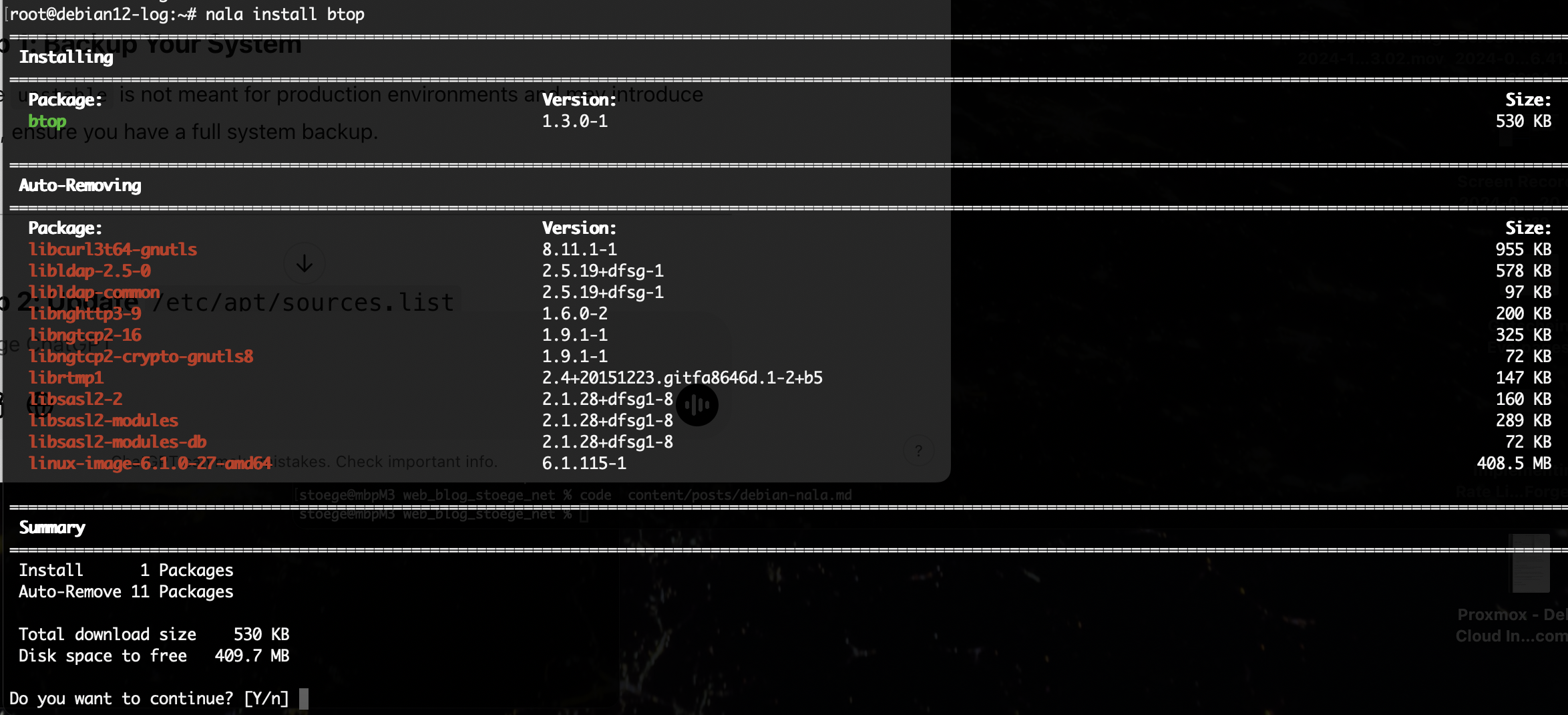
Commands
nala --help
│ autopurge Autopurge packages that are no longer needed. │
│ autoremove Autoremove packages that are no longer needed. │
│ clean Clear out the local archive of downloaded package files. │
│ fetch Fetch fast mirrors to speed up downloads. │
│ full-upgrade Upgrade the system by removing/installing/upgrading packages. │
│ history Show transaction history. │
│ install Install packages. │
│ list List packages based on package names. │
│ purge Purge packages. │
│ remove Remove packages. │
│ search Search package names and descriptions. │
│ show Show package details. │
│ update Update package list. │
│ upgrade Upgrade the system by upgrading packages only.
Commands
nala list list all packages
nala list -i list installed packages
nala list -N list packages installed with nala
nala list -u list upgradable packages
nala list -h show help for all list commands ...
Any Comments ?
sha256: 831a68cb00e13085f9eab36dcab94139961c2b083479df6874fd640d0e7ee883